The Power of AI in DevSecOps: Building Secure Applications Faster
- 7 minutes read - 1458 wordsAs artificial intelligence (AI) rapidly advances, its profound implications for these practices offer unprecedented opportunities to further strengthen our security posture and streamline processes.
In this post I will focus on the transformative integration of DevSecOps and how the shift-left philosophy has fundamentally enhanced how organizations approach security throughout the software development lifecycle.
Understanding DevSecOps and Shifting Left
DevSecOps integrates security practices within the DevOps process, ensuring that security is a shared responsibility throughout the software development lifecycle.
Take a look at this real work example - Deploying a web application on AWS EC2: CI/CD Pipeline with Security Checks.
High Level Overview
This CI/CD pipeline deploys a Java application (target/WebApp.war) on a Tomcat web server. It incorporates security checks as part of a DevSecOps approach.
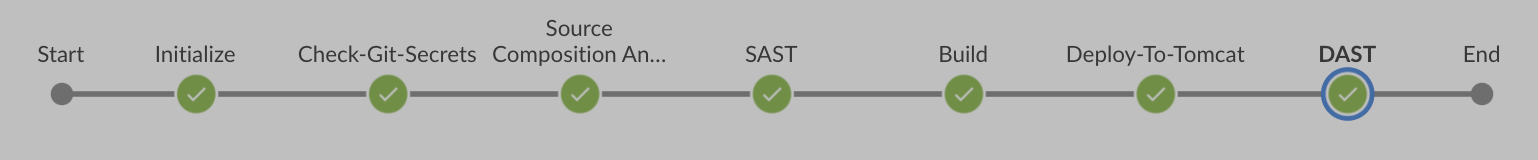
Image Source: d0uble3l. “DevSecOps - Implementing Secure CI/CD Pipelines” GitHub.
Tools
- Jenkins: CI/CD Pipeline
- GitHub: Source Code Manager
- TruffleHog: Secrets Scanner (Docker) - Example Below
- OWASP Dependency-Check: Software Composition Analysis (SCA) (Bash script) - Example Below
- SonarQube: Static Application Security Testing (SAST) (Docker container)
- Maven: Build Tool (running on instance)
- Tomcat: Web HTTP Server that runs Java code (running on instance)
- OWASP ZAP: Dynamic Application Security Testing (DAST) (running on Docker)
pipeline {
agent any
tools {
maven 'Maven'
}
stages {
stage ('Initialize') {
steps {
sh '''
echo "PATH = ${PATH}"
echo "M2_HOME = ${M2_HOME}"
'''
}
}
stage ('Check-Git-Secrets') {
steps {
sh 'rm trufflehog || true'
sh 'docker run gesellix/trufflehog --json https://github.com/d0uble3L/webapp.git > trufflehog'
sh 'cat trufflehog'
}
}
stage ('Source Composition Analysis') {
steps {
sh 'rm owasp* || true'
sh 'wget "https://raw.githubusercontent.com/d0uble3L/webapp/master/owasp-dependency-check.sh" '
sh 'chmod +x owasp-dependency-check.sh'
sh 'bash owasp-dependency-check.sh'
sh 'cat /var/lib/jenkins/OWASP-Dependency-Check/reports/dependency-check-report.xml'
}
}
stage ('SAST') {
steps {
withSonarQubeEnv('sonar') {
sh 'mvn sonar:sonar'
sh 'cat target/sonar/report-task.txt'
}
}
}
stage ('Build') {
steps {
sh 'mvn clean package'
}
}
stage ('Deploy-To-Tomcat') {
steps {
sshagent(['tomcat']) {
sh 'scp -o StrictHostKeyChecking=no target/*.war ec2-user@tomcat-server:/home/ec2-user/prod/apache-tomcat-9.0.74/webapps/webapp.war'
}
}
}
stage ('DAST') {
steps {
sshagent(['zap']) {
sh 'ssh -o StrictHostKeyChecking=no ec2-user@zap-server "docker run -t owasp/zap2docker-stable zap-baseline.py -t http://tomcat-server:8080/webapp/" || true'
}
}
}
}
}
Code Source: d0uble3l. webapp/Jenkinsfile, GitHub.
Shifting left means addressing security concerns earlier in development, which helps to reduce vulnerabilities and mitigate risks before deployment.
Securing Dependencies with OWASP Dependency-Check
One of the key steps in ensuring the security of your software is identifying vulnerable third-party libraries.OWASP Dependency-Check is an open-source tool designed to help developers and security professionals automatically identify known vulnerabilities in project dependencies. By scanning your project’s libraries against the National Vulnerability Database (NVD), it provides reports on any potential risks, making it a crucial part of your DevSecOps pipeline.
Integrating OWASP Dependency-Check can significantly enhance your application’s security posture, ensuring you address vulnerabilities before they can be exploited in production.
Example: OWASP Dependency-Check in Action
For a practical implementation of OWASP Dependency-Check, check out this example script from my GitHub repo. This script demonstrates how to integrate Dependency-Check into your pipeline to scan for vulnerabilities in project dependencies.
#!/bin/sh
OWASPDC_DIRECTORY=$HOME/OWASP-Dependency-Check
DATA_DIRECTORY="$OWASPDC_DIRECTORY/data"
REPORT_DIRECTORY="$OWASPDC_DIRECTORY/reports"
if [ ! -d "$DATA_DIRECTORY" ]; then
echo "Initially creating persistent directories"
mkdir -p "$DATA_DIRECTORY"
chmod -R 777 "$DATA_DIRECTORY"
mkdir -p "$REPORT_DIRECTORY"
chmod -R 777 "$REPORT_DIRECTORY"
fi
# Make sure we are using the latest version
docker pull owasp/dependency-check
docker run --rm \
--volume $(pwd):/src \
--volume "$DATA_DIRECTORY":/usr/share/dependency-check/data \
--volume "$REPORT_DIRECTORY":/report \
owasp/dependency-check \
--scan /src \
--format "ALL" \
--project "My OWASP Dependency Check Project" \
--out /report
# Use suppression like this: (/src == $pwd)
# --suppression "/src/security/dependency-check-suppression.xml"
Code Source: d0uble3l. webapp/owasp-dependency-check.sh, GitHub.
By automating these checks, you can ensure continuous security for your application dependencies.
Checking Git Secrets in Pipeline Using Trufflehog
When securing your CI/CD pipeline, it’s essential to scan for sensitive information accidentally committed to your repositories. Trufflehog is a powerful regex-based scanning tool designed to detect secrets in your Git history.
Example: Trufflehog in Action
You can quickly run Trufflehog in a Docker container to scan your Git repository for secrets:
# Pull the Trufflehog Docker image
docker pull gesellix/trufflehog
# Run Trufflehog on your GitHub repository
docker run gesellix/trufflehog <GIT REMOTE REPO URL>
# Add the user to the Docker group
sudo usermod -aG docker ec2-user
# Change Docker socket permissions
sudo chmod 666 /var/run/docker.sock
# Restart Jenkins to apply changes
sudo systemctl restart jenkins
Learn More About Trufflehog
For more information on Trufflehog and its features, visit the official Trufflehog GitHub repository. This resource provides documentation, installation instructions, and additional usage examples to help you integrate Trufflehog into your security workflow.
The Role of AI in Enhancing Security Practices

AI technologies are set to revolutionize both DevSecOps and the shift-left strategy in several ways:
Automated Threat Detection: AI can analyze vast amounts of data to identify patterns indicating security threats. This capability allows for real-time monitoring and rapid response, enabling teams to address vulnerabilities as they arise.
Enhanced Vulnerability Management: Machine learning algorithms improve vulnerability scanning by prioritizing threats based on risk levels and exploitability, helping teams focus on the most critical vulnerabilities.
Intelligent Incident Response: AI-driven systems automatically triage security alerts and provide remediation recommendations, speeding up response times and allowing security teams to focus on more complex issues.
Improved Collaboration: AI tools facilitate better collaboration between development, security, and operations teams by providing accessible insights, fostering a culture of shared responsibility for security.
Training and Awareness: AI can personalize security training for developers, enhancing their understanding of security best practices and equipping them to implement secure coding practices from the outset.
Companies Leading the Charge with AI in DevSecOps
Microsoft: With tools like GitHub Copilot and Azure DevOps, Microsoft integrates AI to enhance developer productivity and improve security throughout the DevSecOps pipeline.
Google Cloud: AI powers the Google Cloud Security Command Center, offering automated security insights to secure applications in development and deployment.
IBM: IBM Watson for Cybersecurity and Red Hat OpenShift leverage AI to detect security threats and automate security checks early in the DevSecOps process.
Snyk: Snyk offers AI-powered security scanning for open-source dependencies, containers, and IaC, empowering teams to address vulnerabilities early in development.
Palo Alto Networks: Prisma Cloud uses AI and machine learning to secure cloud-native applications, identifying vulnerabilities across the development lifecycle.
Checkmarx: Checkmarx integrates AI-powered application security testing to automate code reviews and security checks, aligning with the shift-left philosophy.
Darktrace: Darktrace uses AI to autonomously detect and respond to cyber threats, securing the development process against malicious activity.
By adopting AI-driven tools, these companies are transforming how security is integrated into development workflows, enabling teams to shift security left and enhance overall security posture.
Further Reading
Transform Your Development Process with Our Guide

To help you navigate the integration of security into your development processes, consider exploring Code, Commit, Secure - DevSecOps In Action. This comprehensive guide is designed to empower you with the principles, practices, and real-world examples necessary for building secure and resilient software.
What You’ll Discover
- Foundational Principles: Understand the core tenets of DevSecOps and their critical importance.
- Real-World Case Studies: Explore in-depth examples of successful DevSecOps implementations across various industries.
- Actionable Tips: Gain practical guidance for starting and scaling DevSecOps initiatives in your organization.
- Tools and Techniques: Discover the latest tools for automating security testing and continuous monitoring.
- Risk Mitigation Strategies: Learn how to effectively address common risks inherent in traditional DevOps.
Why This Guide Matters
Developed by industry experts, this resource offers practical insights and actionable steps that you can apply immediately. Whether you’re a developer, security professional, operations team member, or a manager looking to drive organizational change, this guide is designed to meet your needs*.
Download Now: Code, Commit, Secure - DevSecOps In Action
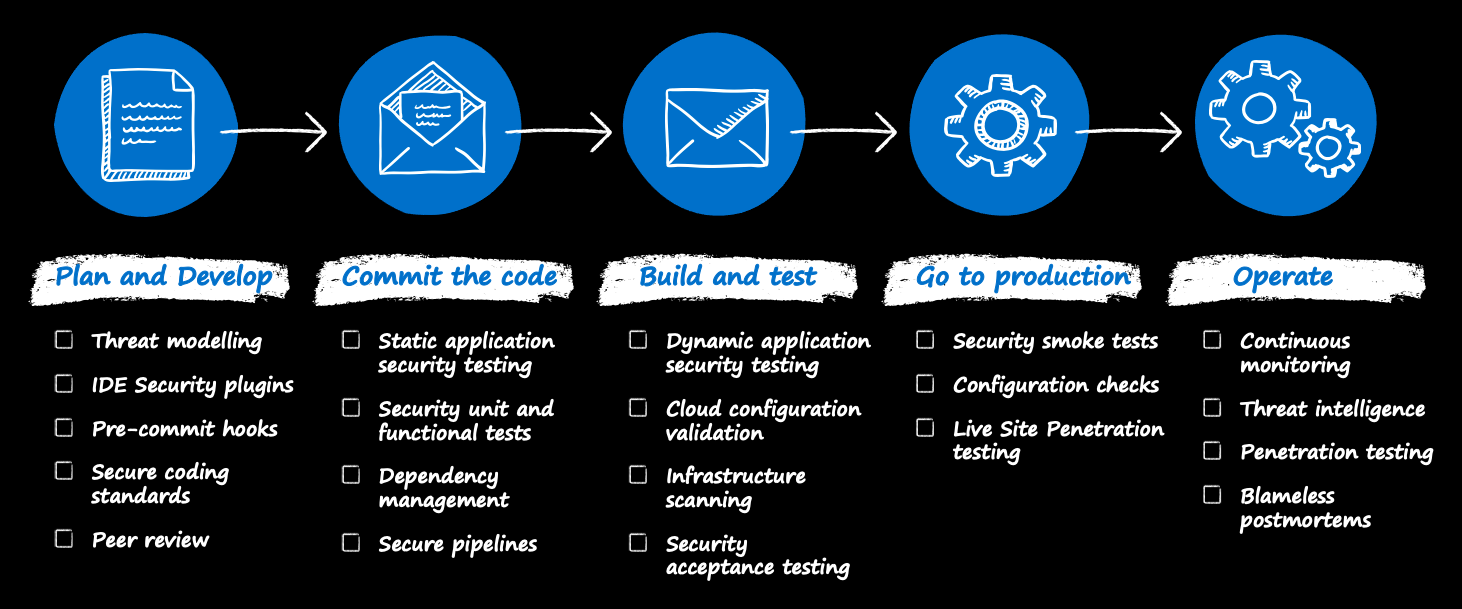 Image Source: DevSecOps Guides. “Methodology.” DevSecOps Guides.
Image Source: DevSecOps Guides. “Methodology.” DevSecOps Guides.
Challenges and Considerations
While AI integration presents significant opportunities, it also introduces challenges. Organizations must ensure AI models are trained on high-quality, diverse datasets to avoid biases.
Furthermore, reliance on AI should not diminish the importance of human oversight; a balanced approach that combines automated processes with human intuition is essential.
To Wrap Up
The convergence of AI, DevSecOps, and the shift-left philosophy marks a transformative era in cybersecurity. By leveraging AI technologies, organizations can enhance their security posture and cultivate a culture of security awareness throughout the development lifecycle.
Start transforming your development process with Code, Commit, Secure - DevSecOps In Action and take the first step toward becoming a DevSecOps champion in your organization!
Thanks for reading,
Michael
If you enjoy the content, then consider buying me a coffee.
P.S. Stay updated on the latest cybersecurity trends and best practices by subscribing to our newsletter or leaving your thoughts in the comments below! Visit CyberSHIELD